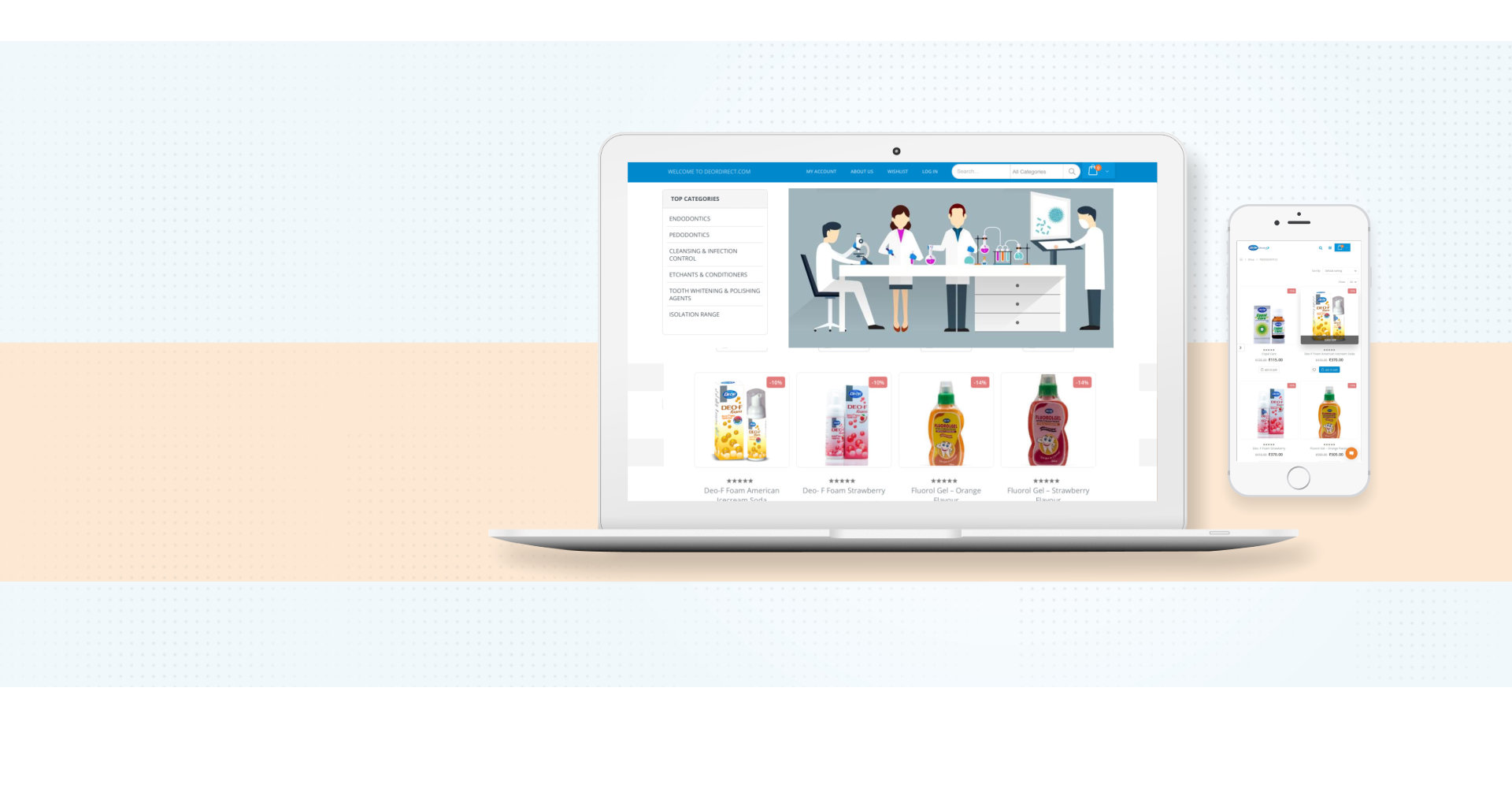
Our Services
IT services and strategies. IT support and management. IT specialists of all stripes, working offshore or onsite. From website and mobile app development to QA and testing, a comprehensive set of solutions for all things in IT.
E-commerce
Utilising advanced E-commerce design techniques, Bitsping can convert your website into a fully-fledged interactive sales platform, complete with shopping cart functionality and a payment verification gateway. …
Read MoreMobile Applications
Bitsping Technologies gives extensive answers for Android App Development in ventures like Business, Finance, Education and Health Care. Our elevated requirements, focused cost and group of Top Android App …
Read MoreWebsite Designing
Designing websites is not just about digital decoration; it’s about delivering your brand to the world in a clear, concise and usable way based on project goals and return on investment.Bitsping offers a variety of web planning and advancement answers …
Read MoreWeb Application Development
Bitsping is one of the astounding and rich site planning and site Development Company in Cochin, India, with a group of to a great degree exceptionally originators, engineers and advertisers available to you. ..
Read MoreOur Recent Works
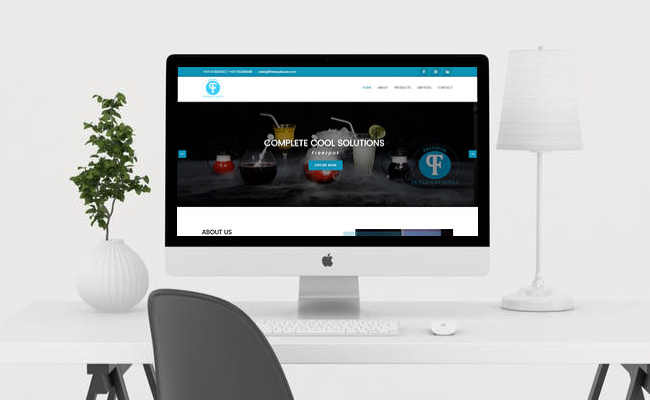
Woodhaven.in
Based out of Cochin,India, Woodhaven specialize in building wooden homes, interiors, flooring and cottages out of seasoned wood of your choice. We create marvels out of wood that’s equally charming, warm and full of life. We bring nature closer to you! We have expert teams that are specialized in designing your dreams
Read More